General Info
| Rank: | #40 Worldwide #4 outside of US and Europe |
|---|---|
| Papers: | 68 |
| Number of Researchers: | 115 |
| APA (average papers per authors): |
0.6 |
| Country: | SINGAPORE |
| Rank: | #40 Worldwide #4 outside of US and Europe |
|---|---|
| Papers: | 68 |
| Number of Researchers: | 115 |
| APA (average papers per authors): |
0.6 |
| Country: | SINGAPORE |
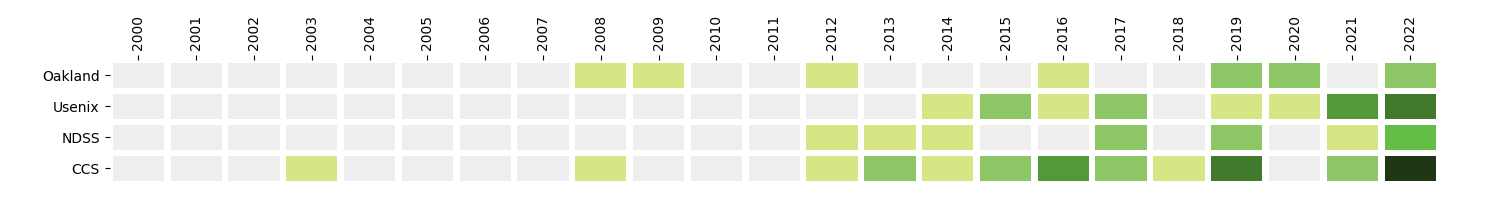
Mohan S. Kankanhalli, ... -- CCS 2003
Haifeng Yu, Feng Xiao, ... -- Oakland 2008
Wei Wang, Mehul Motani, ... -- CCS 2008
Haifeng Yu, Feng Xiao, Chenwei Shi, ... -- Oakland 2009
Mingwei Zhang, Xiaolei Li, Zhenkai Liang, ... -- NDSS 2012
Zhenkai Liang, ... -- Oakland 2012
Haifeng Yu, ... -- CCS 2012
Guangdong Bai, Guozhu Meng, Jike Lei, Sai Sathyanarayan Venkatraman, Prateek Saxena, Jinsong Dong, ... -- NDSS 2013
Shruti Tople, Shweta Shinde, Prateek Saxena, Zhaofeng Chen, ... -- CCS 2013
Xinshu Dong, Shruti Tople, Prateek Saxena, Zhenkai Liang, ... -- CCS 2013
Zhenkai Liang, ... -- NDSS 2014
Minh-Thai Trinh, Duc-Hiep Chu, Joxan Jaffar, ... -- CCS 2014
Zheng Leong Chua, Prateek Saxena, ... -- Usenix 2014
Loi Luu, Jason Teutsch, Raghav Kulkarni, Prateek Saxena, ... -- CCS 2015
Pratik Soni, Enrico Budianto, Prateek Saxena, ... -- CCS 2015
Hong Hu, Zheng Leong Chua, Sendroiu Adrian, Prateek Saxena, Zhenkai Liang, ... -- Usenix 2015
Anh Dinh, Prateek Saxena, Chang Ee-chien, Zhang Chunwang, Ooi Beng Chin, ... -- Usenix 2015
Hong Hu, Shweta Shinde, Adrian Sendroiu, Zheng Leong Chua, Prateek Saxena, Zhenkai Liang, ... -- Oakland 2016
Loi Luu, Duc-Hiep Chu, Prateek Saxena, Aquinas Hobor, ... -- CCS 2016
Loi Luu, Viswesh Narayanan, Chaodong Zheng, Kunal Baweja, Seth Gilbert, Prateek Saxena, ... -- CCS 2016
Yaoqi Jia, Zheng Leong Chua, Hong Huang, Prateek Saxena, Zhenkai Liang, ... -- CCS 2016
Marcel Boehme, Van-Thuan Pham, Abhik Roychoudhury, ... -- CCS 2016
Yaoqi Jia, Shruti Tople, Prateek Saxena, ... -- Usenix 2016
Shweta Shinde, Dat Le Tien, Shruti Tople, Prateek Saxena, ... -- NDSS 2017
Gregory J. Duck, Roland H. C. Yap, ... -- NDSS 2017
Marcel Bohme, Van-Thuan Pham, Manh-Dung Nguyen, Abhik Roychoudhury, ... -- CCS 2017
Hung Dang, Huang Yue, Ee-Chien Chang, ... -- CCS 2017
Zheng Leong Chua, Shiqi Shen, Prateek Saxena, Zhenkai Liang, ... -- Usenix 2017
Loi Luu, Prateek Saxena, ... -- Usenix 2017
Reza Shokri, ... -- CCS 2018
Zheng Leong Chua, Teodora Baluta, Prateek Saxena, Zhenkai Liang, ... -- NDSS 2019
Shiqi Shen, Shweta Shinde, Soundarya Ramesh, Prateek Saxena, Abhik Roychoudhury, ... -- NDSS 2019
Reza Shokri, Reza Shokri, ... -- Oakland 2019
Muoi Tran, Min Suk Kang, ... -- Oakland 2019
Xiaokui Xiao, ... -- CCS 2019
Ziqi Yang, Jiyi Zhang, Ee-Chien Chang, Zhenkai Liang, ... -- CCS 2019
Reza Shokri, Reza Shokri, ... -- CCS 2019
Jianting Ning, Geong Sen Poh, Jia-Chng Loh, Jason Chia, Ee-Chien Chang, ... -- CCS 2019
Teodora Baluta, Shiqi Shen, Kuldeep S. Meel, Prateek Saxena, ... -- CCS 2019
Jernej Kos, ... -- Usenix 2019
Muoi Tran, Inho Choi, Min Suk Kang, ... -- Oakland 2020
Haifeng Yu, Ivica Nikolic, Ruomu Hou, Prateek Saxena, ... -- Oakland 2020
Shengyi Wang, Pinghai Yuan, Aquinas Hobor, Abhik Roychoudhury, Prateek Saxena, ... -- Usenix 2020
Jun Zeng, Kaihang Ji, Zhenkai Liang, ... -- NDSS 2021
Jinhua Cui, Zhijingcheng Yu, Prateek Saxena, ... -- CCS 2021
Aashish Kolluri, Teodora Baluta, Prateek Saxena, ... -- CCS 2021
Muoi Tran, Akshaye Shenoi, ... -- Usenix 2021
Soundarya Ramesh, Rui Xiao, Jong Taek Lee, Harini Ramprasad, Ananda Kumar, Jun Han, ... -- Usenix 2021
Yun Lin, Ruofan Liu, Jun Yang Ng, Qing Zhou Chan, Jin Song Dong, ... -- Usenix 2021
Nitya Lakshmanan, Nishant Budhdev, Mun Choon Chan, Jun Han, ... -- Usenix 2021
Pengfei Wu, Ee-Chien Chang, Hongbin Wang, Jiamin Shen, ... -- NDSS 2022
Pengfei Wu, Jiamin Shen, Hongbing Wang, Ee-Chien Chang, ... -- NDSS 2022
Pengfei Wu, ... -- NDSS 2022
Jun Zeng, Xiang Wang, Jiahao Liu, Zhenkai Liang, Tat-Seng Chua, ... -- Oakland 2022
Ruomu Hou, Haifeng Yu, Prateek Saxena, ... -- Oakland 2022
Jianxin Wei, Ergute Bao, Xiaokui Xiao, ... -- CCS 2022
Jiayuan Ye, Aadyaa Maddi, Reza Shokri, ... -- CCS 2022
Xinjian Luo, Yangfan Jiang, Xiaokui Xiao, ... -- CCS 2022
Aashish Kolluri, Teodora Baluta, Bryan Hooi, Prateek Saxena, ... -- CCS 2022
Teodora Baluta, Shiqi Shen, S. Hitarth, Shruti Tople, Prateek Saxena, ... -- CCS 2022
Jun Zeng, Chuqi Zhang, Zhenkai Liang, ... -- CCS 2022
Soundarya Ramesh, Ghozali Suhariyanto Hadi, Mun Choon Chan, ... -- CCS 2022
Reza Shokri, ... -- CCS 2022
Jason Zhijingcheng Yu, Trevor E. Carlson, Prateek Saxena, ... -- Usenix 2022
Ruofan Liu, Yun Lin, Xianglin Yang, Siang Hwee Ng, Jin Song Dong, ... -- Usenix 2022
Zhenkai Liang, ... -- Usenix 2022
Jinsheng Ba, Abhik Roychoudhury, ... -- Usenix 2022
Kaihang Ji, Jun Zeng, Yuancheng Jiang, Zhenkai Liang, Prateek Saxena, Abhik Roychoudhury, ... -- Usenix 2022