Bluetooth traffic analysis
Introduction
Overview
In this part, we introduce the Bluetooth Low Energy protocol and how to use Wireshark and BlueZ to monitor packets.
Bluetooth Low Energy stack
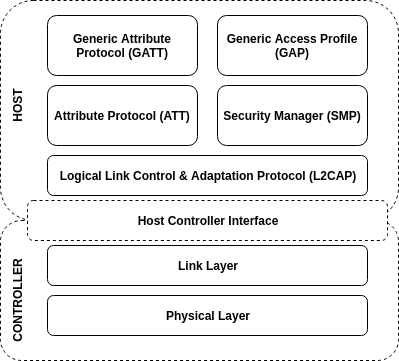
A typical Bluetooth Low Energy stack is splitted in two main parts:
- Host: handles the upper layers - Logical Link Control and Adaptation Protocol (L2CAP, shared with Bluetooth Classic), Attribute Protocol (ATT), Generic Attribute Protocol (GATT), Security Manager (SMP) and Generic Access Profile (GAP),
- Controller: handles the lower layers - Link Layer (LL) and Physical Layer.
During a Bluetooth Low Energy operation, the Host transmits HCI commands to the Controller and receives HCI events from it. Several solutions exists to monitor these commands and events, allowing to facilitate the analysis of the protocol.
Monitoring HCI traffic
The first solution is to use the utility named btmon, provided by BlueZ stack. To test it, you can run in a first terminal the following command:
cyberinsophia@vm:~$ sudo btmon -i hci0
Bluetooth monitor ver 5.64
= Note: Linux version 5.18.5-100.fc35.x86_64 (x86_64) 0.447778
= Note: Bluetooth subsystem version 2.22 0.447781
= New Index: 94:E2:3C:62:C0:40 (Primary,USB,hci0) 0.447783
= Open Index: 94:E2:3C:62:C0:40 0.447783
= Index Info: 94:E2:3C:62:C0:40 (Intel Corp.) 0.447784
@ MGMT Open: bluetoothd (privileged) version 1.22
In a second terminal, we will run a LE scan operation. It will allow us to identify our ESP32 which is currently transmitting advertisements in broadcast to indicate its presence:
cyberinsophia@vm:~$ sudo hcitool lescan
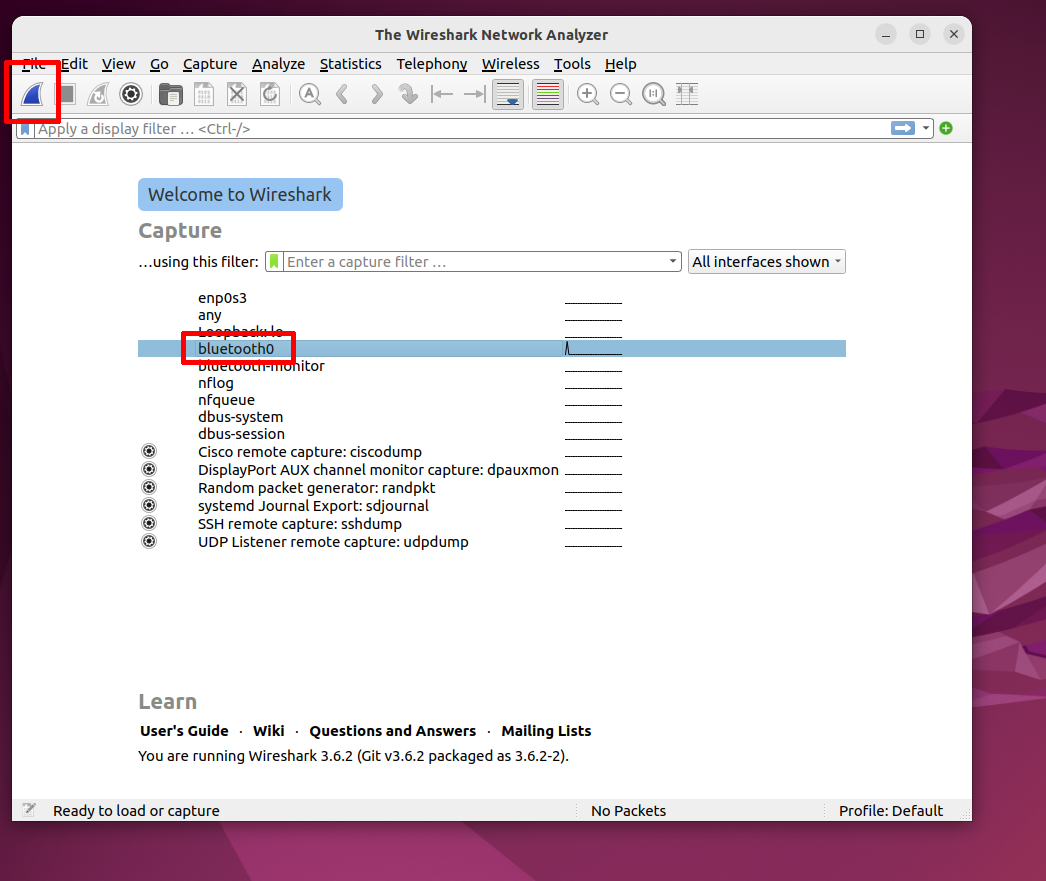
cyberinsophia@vm:~$ sudo wireshark
bluetooth0 in the list and click on the start button.
Communicating with ESP32
Bluetooth Low Energy roles
Now, we are ready to establish a BLE connection with our ESP32 peripheral. We will use wireshark to monitor HCI commands and events and observe the pairing process during these operations.
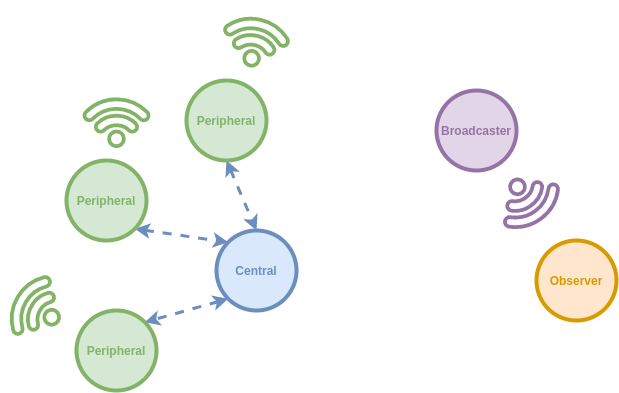
In Bluetooth Low Energy, a device can act according to four main roles:
- Broadcaster / Advertiser: the device is only able to transmit advertisements,
- Observer / Scanner: the device is only able to scan advertisements,
- Peripheral: the device is able to transmit advertisements and accept incoming connection,
- Central: the device is only able to scan advertisements and initiate connections.
Establishing a BLE connection
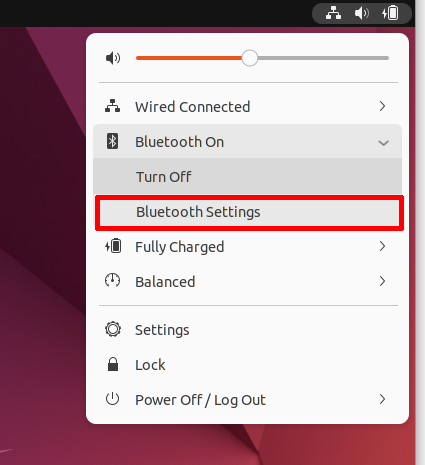
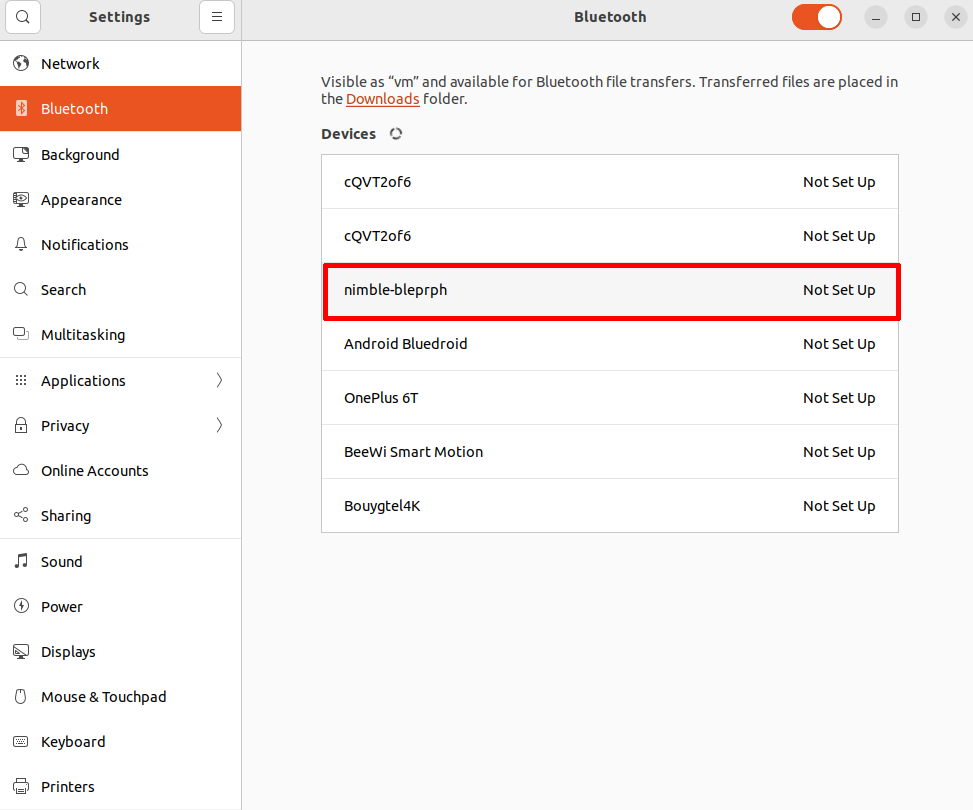
First, open Bluetooth settings using the Gnome interface:

Monitoring Bluetooth Low Energy Pairing
Observing negotiation
Bluetooth Low Energy pairing starts by negotiating the security parameters, thanks to a Pairing Request and a Pairing Response:
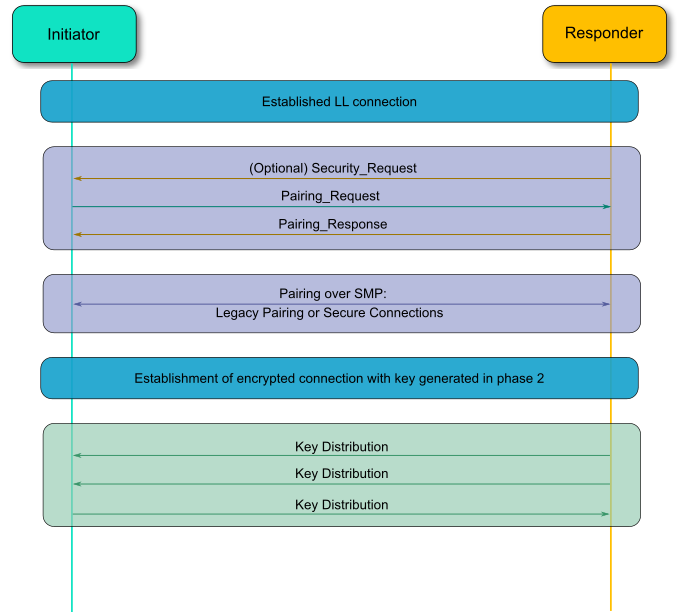
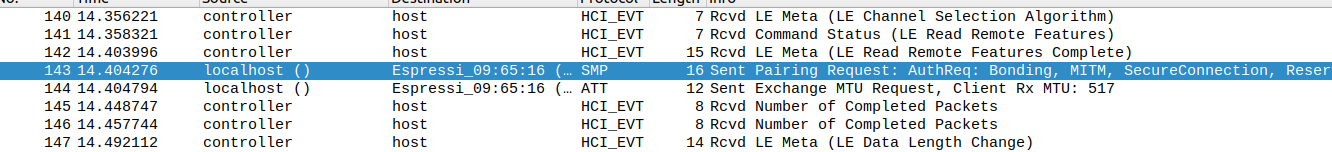
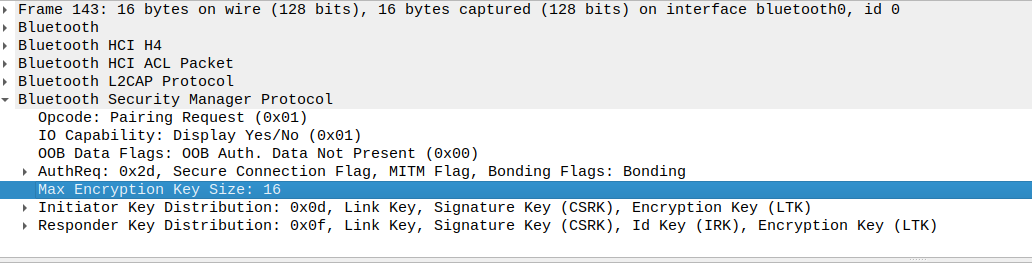
Now, identify the Pairing Response transmitted by the ESP32 Peripheral:
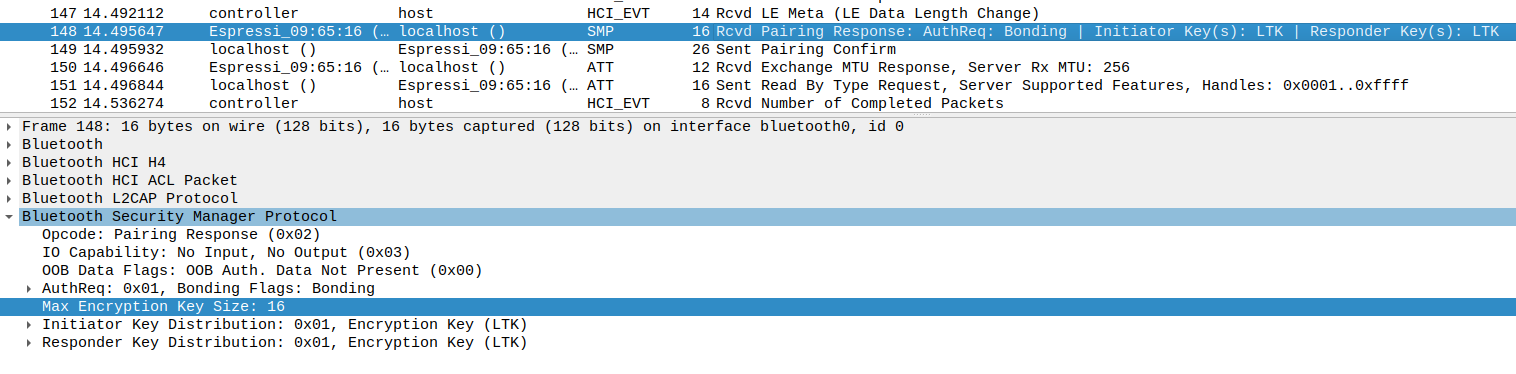
Observing Legacy Pairing
In this case, ESP32 is not configured to use LE Secure Connections pairing, so the Legacy Pairing will be used :
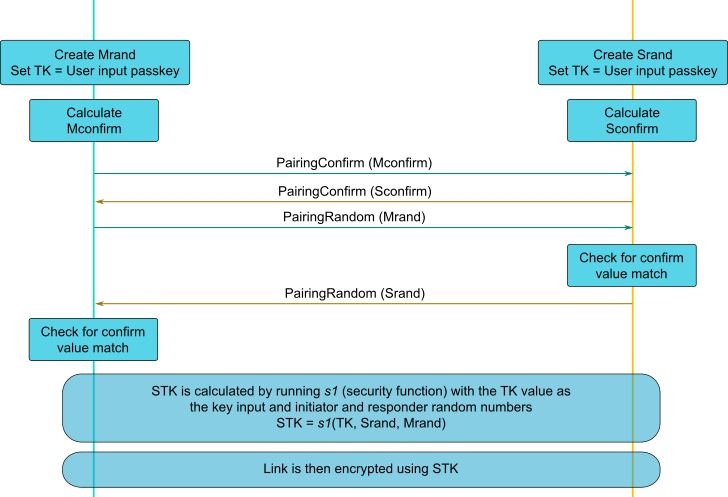
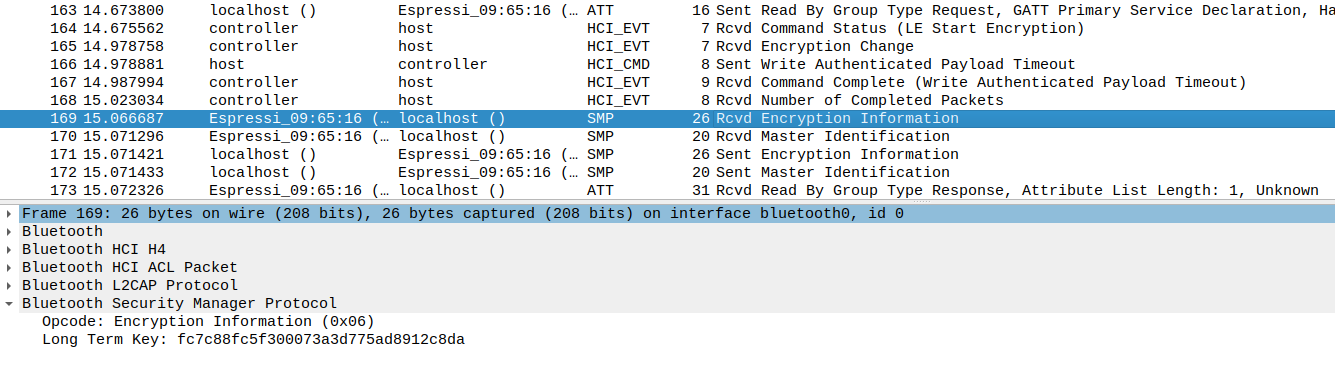
Based on the random values and the Temporary Key, a Short Term Key can now be calculated on both side, allowing the Link to be encrypted. You can observe the Encryption being enabled in Wireshark using LE Start Encryption command.
Observing Key Distribution
Once the link has been encrypted, the devices will transmit their respective keys according to the negotiated key distribution: